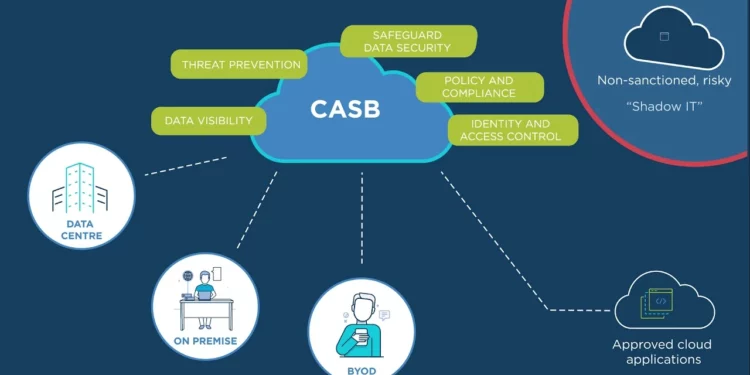
A CASB enables businesses to secure access to cloud resources, including software as a Service (SaaS), Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) apps.
A CASB helps enforce security policies across an organization’s cloud apps using APIs, gateways, log data, and agents. These tools can also help IT teams identify cloud applications that need additional protection, like malware prevention.
Classification
As more organizations turn to cloud-based software and services, they face the challenge of safeguarding sensitive information. Using a CASB helps to monitor all of these risks and ensure data security.
A CASB can provide visibility into cloud application usage and help organizations determine which applications employees use and if they are authorized. It enables them to protect data, users, and intellectual property with providers like Versa Networks.
CASBs also have a broader scope of policy enforcement than traditional security solutions. They can authenticate users, enforce data loss prevention (DLP), and protect against malware.
They also monitor activity across various applications, including social media and SaaS apps. It helps organizations keep sensitive information secure and comply with critical compliance regulations.
A CASB can use machine learning to identify abnormal user behavior and assess the risk associated with an application. It can allow businesses to understand their current security environment and implement improvements to prevent future threats and breaches.
A CASB can be a valuable tool for enterprises that have adopted the cloud-based work model, but it must be appropriately implemented to ensure that data is not compromised. For instance, schools and educational institutes must protect their students’ information from potential breaches that could jeopardize student records and academic outcomes.
Remediation
A cloud-based policy enforcement hub known as a cloud access security broker (CASB) combines and enacts various security policies for all networked devices. They help companies maintain security in the cloud, enabling users to connect securely and access enterprise data from anywhere.
Remediation is a core function of a CASB, offering capabilities to identify and remediate unauthorized or malicious activity in the cloud. Specifically, a CASB can help to detect and remediate malware, ransomware, file exfiltrations, and more.
Using static and dynamic analysis, UEBA technology, machine learning and threat intelligence, a CASB can scan and analyze cloud services in real-time. It allows it to pinpoint anomalous activities and threats, resulting in better security for your data.
A CASB can provide granular visibility and control over user access to enterprise data in the cloud as an added benefit. It enables the creation of data loss prevention (DLP) tools and processes that can be integrated into your company’s security strategy.
Classification is also a critical CASB functionality, as it allows you to differentiate between sanctioned and unsanctioned SaaS tenants, applying appropriate policies to each. A CASB can also help you manage collaboration and sharing across your cloud apps.
Whether you’re storing sensitive customer information or intellectual property in the cloud, you must ensure that your organization has a comprehensive cloud security solution. A CASB can help you achieve this by providing classification, alerts, monitoring and remediation capabilities.
Alerts
CASBs can provide many alerts to help organizations maintain cloud security. These include suspicious login attempts, data loss prevention alerts and dashboards that help administrators see a complete picture of their safety.
Unlike firewalls, which filter network traffic, CASBs provide visibility into cloud usage and enforce security policies based on that information. Using a combination of policy and user behavior analysis, a CASB helps organizations identify suspicious activities, mitigate them and send alerts to administrators for further action.
A CASB can also help organizations ensure compliance with various regulations governing the privacy and safety of data. For example, a healthcare organization that needs to comply with HIPAA must ensure that only authorized users can access sensitive data. A CASB helps ensure compliance while protecting the business and its clients from costly breaches.
Cybercriminals often use compromised accounts in the cloud to gain access to corporate data and apps. Typically, they begin by trying to guess user passwords with brute force attacks or credential phishing.
For this reason, a cloud security solution must provide visibility into all cloud applications, sanctioned and unsanctioned, to help you keep your data secure. CASBs can also give you robust data control by limiting or allowing access based on location, device type, employee status and more.
Monitoring
CASBs monitor cloud services and endpoints, allowing enterprises to secure data in real-time. They also provide visibility into sanctioned and unsanctioned cloud application usage, called Shadow IT, to help ensure compliance with security policies and regulations.
Employees increasingly use their devices to access business information, and organizations often need more visibility into this behavior. As a result, unauthorized cloud applications and data can breach security measures.
To combat this problem, a CASB continuously monitors the organization’s AWS workload and alerts IT when risky behaviors occur. It enables IT administrators to create and enforce security policies for all cloud services in their environment.
For example, if the CASB sees an employee sharing files on an unsanctioned app, it can prompt security staff to block the app and data from accessing corporate resources.
A CASB identifies and controls risks in cloud applications, data, and endpoints by analyzing traffic. It classifies cloud services based on the level of threat they pose. It uses this information to shape more granular controls, such as allowing or blocking access based on user ID, location, job function, or device.
CASBs also offer advanced threat protection capabilities, such as anti-phishing and malware detection. These features can help prevent data leaks and ensure only authorized users can access cloud-based data.
Also, Read: The Benefits of Wearing Beaded Necklaces – More Than Just Fashion